What is a DOS attack?
A Denial of Service (DoS) attack is a cyber security threat that is directed towards devices, information systems, or other networks that prevent legitimate users from accessing the service or resource.
A Denial of Service (DoS) attack is a cyber security threat that is directed toward devices, information systems, or other networks that prevent legitimate users from accessing the service or resource. A DoS attack can be launched out of malice to disgruntle a business’s operation or as a distraction by the attacker as they launch another attack on the system to steal data or money.
How does it work?
A DoS attack is made by exploiting a software’s vulnerability and seeking to overload the network with a massive number of requests or by sending malicious requests that cause the system to crash or be unable to respond. DoS attacks have been increasing as consumers and businesses continue to be more reliant on digital platforms to communicate; thus, it has evolved to appear in different forms that are described below.
Types of DoS attacks
Buffer flow: The attacker sends more traffic to the target than the developers intended the system to handle. This version of an attack enables the hacker to crash or interfere with the system.
Volumetric attack: Attempts to consume the bandwidth of the network by flooding it with false requests.
SYN Flood attacks: An attacker sends a request to the network but does not authenticate or finalize their connection. This is done until the server is forced to crash.
ICMP flood: The attacker seeks out a misconfigured node on the network and uses this device to target the rest of the network by forcing it to redistribute fake packets to the other nodes on the network.
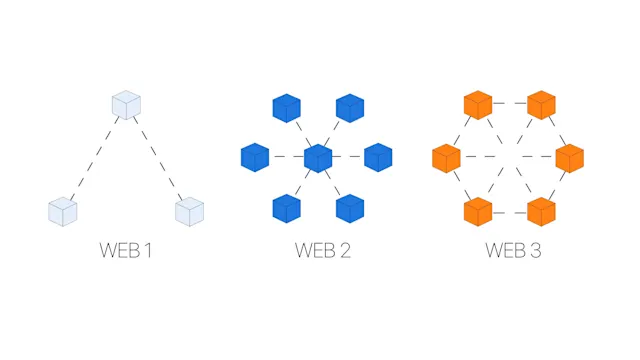
DOS vs. DDOS
In recent times, hackers have opted to use a distributed approach to complete their attack because it is more effective, known as a Distributed DoS (DDoS). The difference between a DoS and a DDoS attack is that an attacker uses multiple machines to direct their attack to a single network. A DDoS is more likely to succeed because it is increasingly difficult to trace the source of the attack since it originates from multiple points.
DOS and Cryptocurrencies
Any device, network, or server connected to the internet can be targeted for the above attacks. With the growing demand for cryptocurrencies, crypto exchanges have become a major target. However, the decentralized structure of the blockchain creates protection against DDoS and DoS attacks. Even if several nodes are compromised, the rest of the nodes can continue to function and later update the affected nodes. Having more nodes and a higher hash rate makes the network more resilient to cyber-attacks; the Bitcoin ($BTC) blockchain is the most decentralized, thus, the most secure and resilient blockchain. This means that DoS and other cyber attacks are less likely to disrupt the network's ability to function.